Pre:
来自朋友的需求,bp项目方某个钱包地址每隔一段时间就会回购宝石代币要监控该钱包回购的动作
脚本:
思路:
一开始打算用爬虫,不过想起之前写rarity的升级脚本调用过ftmscan的api
所以看了一下bscscan的api文档,找到个方法能满足需求
Get a list of 'Normal' Transactions By Address获取地址的交易记录
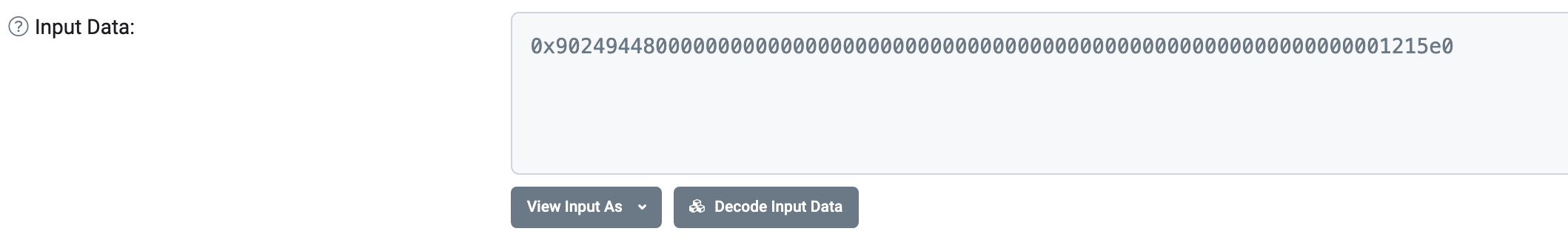
解析input data:
https://api.bscscan.com/api?module=account&action=txlist&address=0xF426a8d0A94bf039A35CEE66dBf0227A7a12D11e&startblock=0&endblock=99999999&page=1&offset=10&sort=asc&apikey=YourApiKeyToken
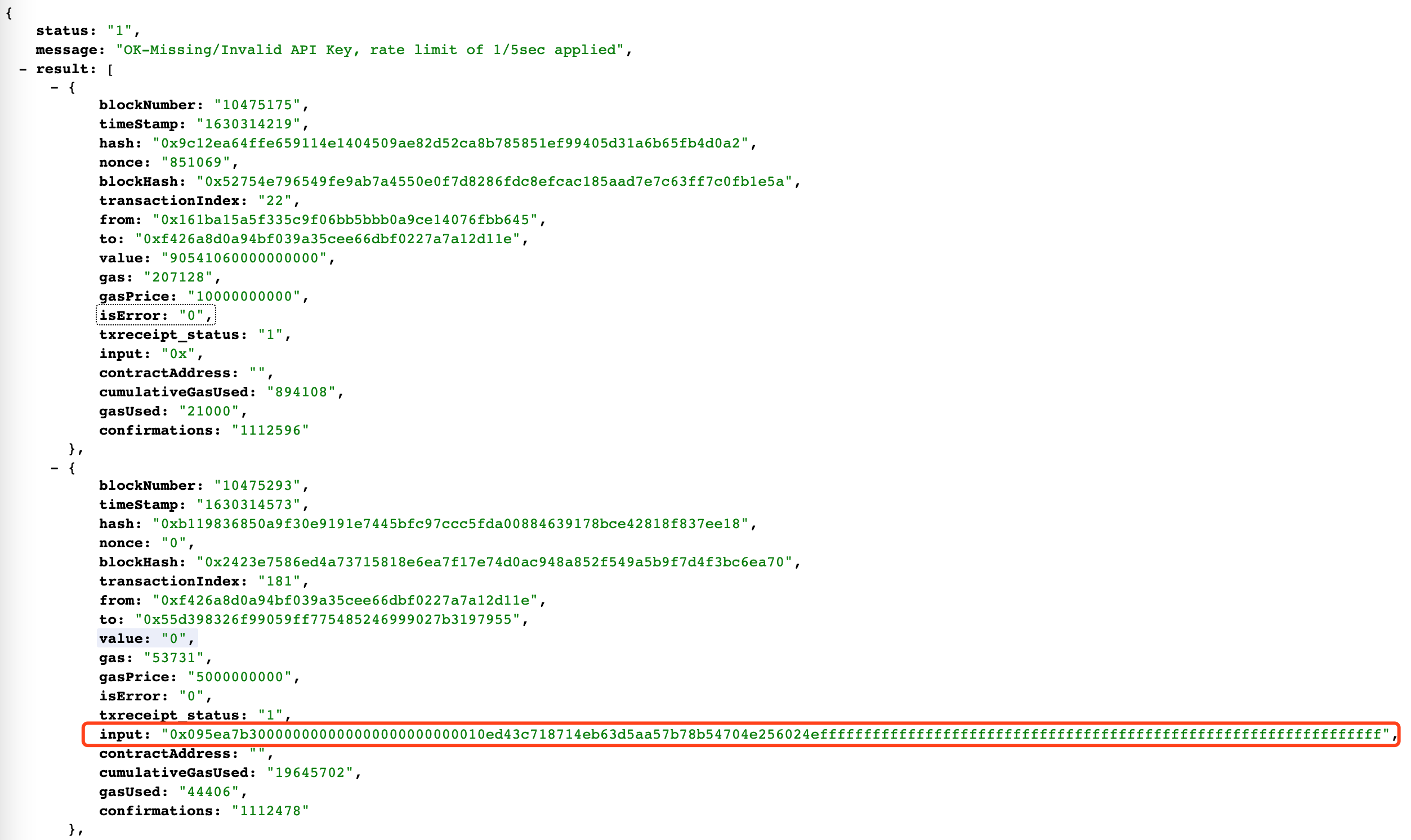
api获取到json结果,本来想拿到它的hash再去进一步查询,但是看到input的数据,这里面其实也是包含了交易的内容,可以尝试去decode这些数据。
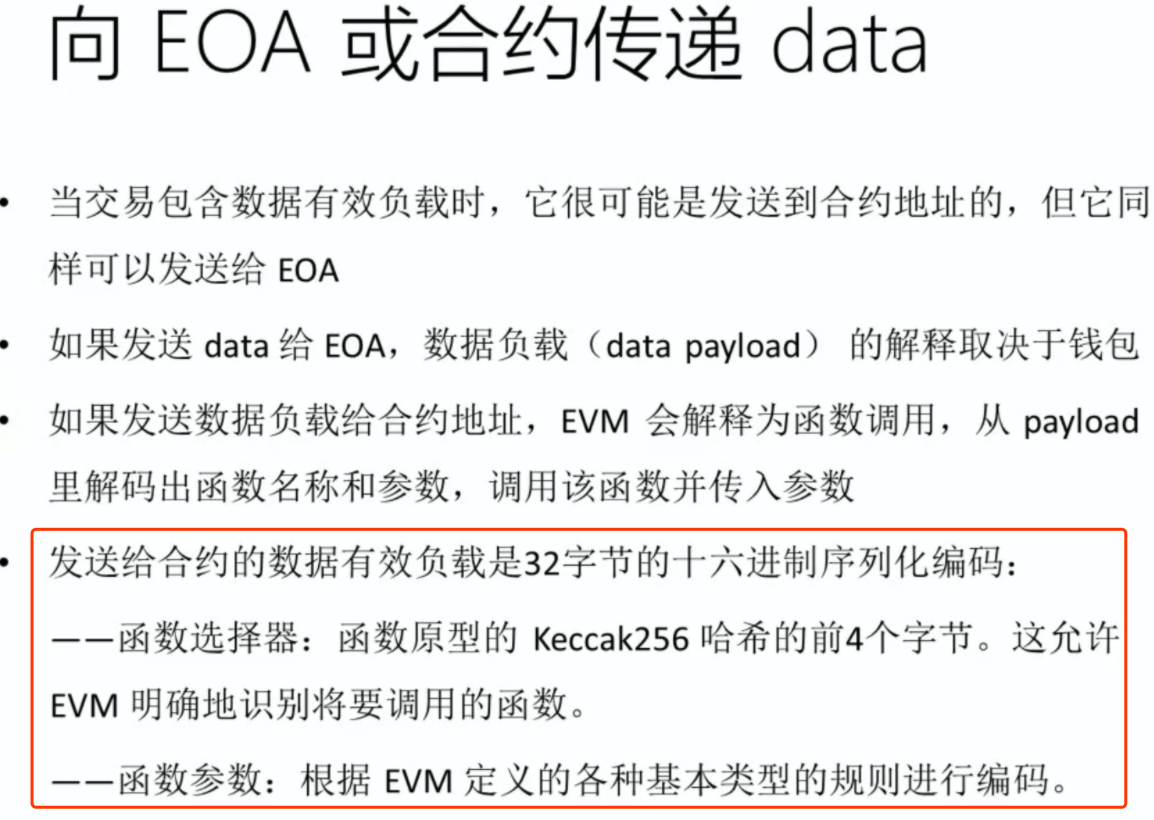
How to decode input data from a transaction?
搜索了一下,似乎是可以定义contract对象,调用函数直接decode
1 | contract.decode_function_input(transaction.input) |
每次回购动作,都是去跟合约交互
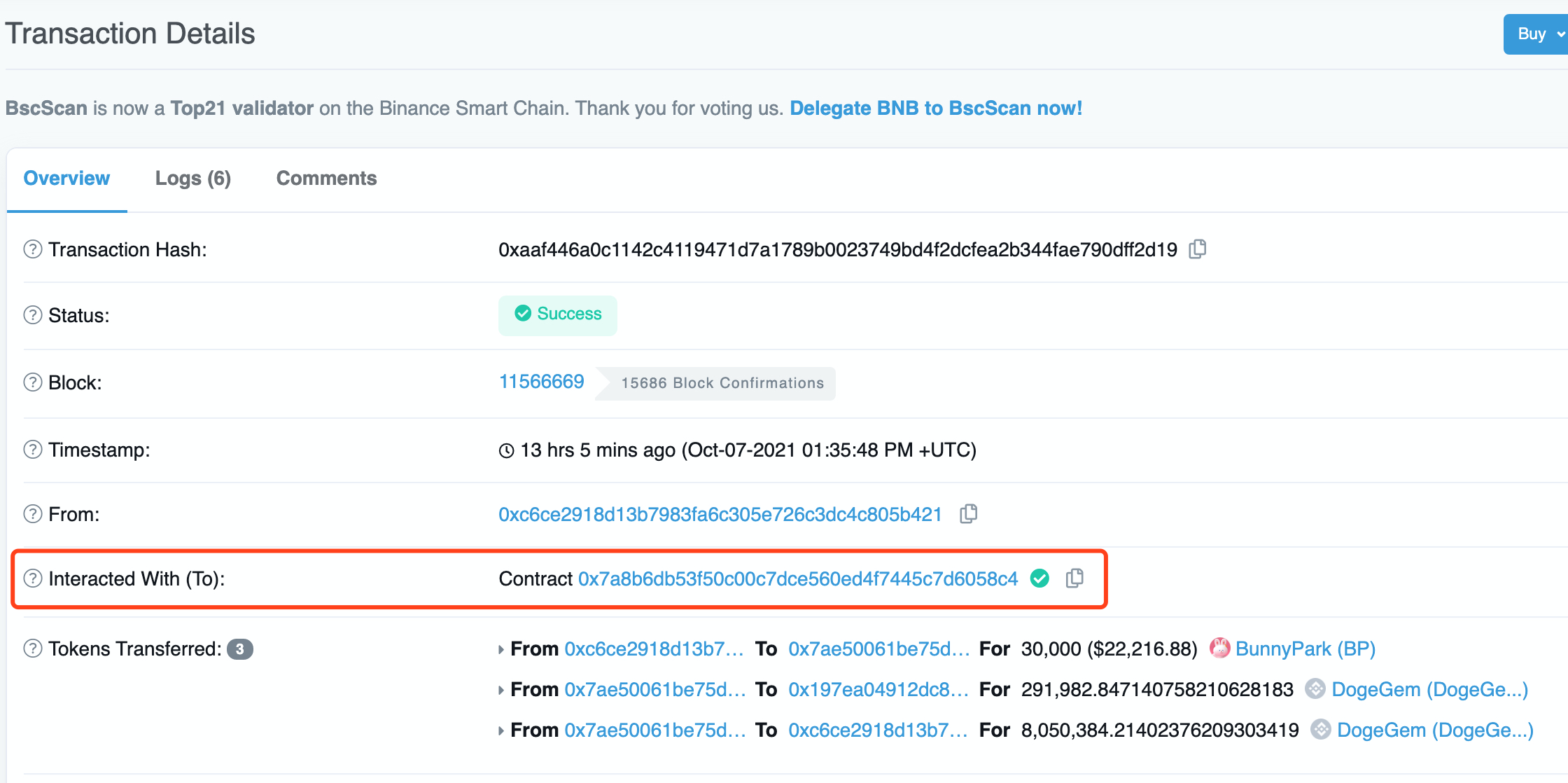
但是这个合约没有开源,没法拿到abi,没法获得contract对象,似乎就没法直接去decode。
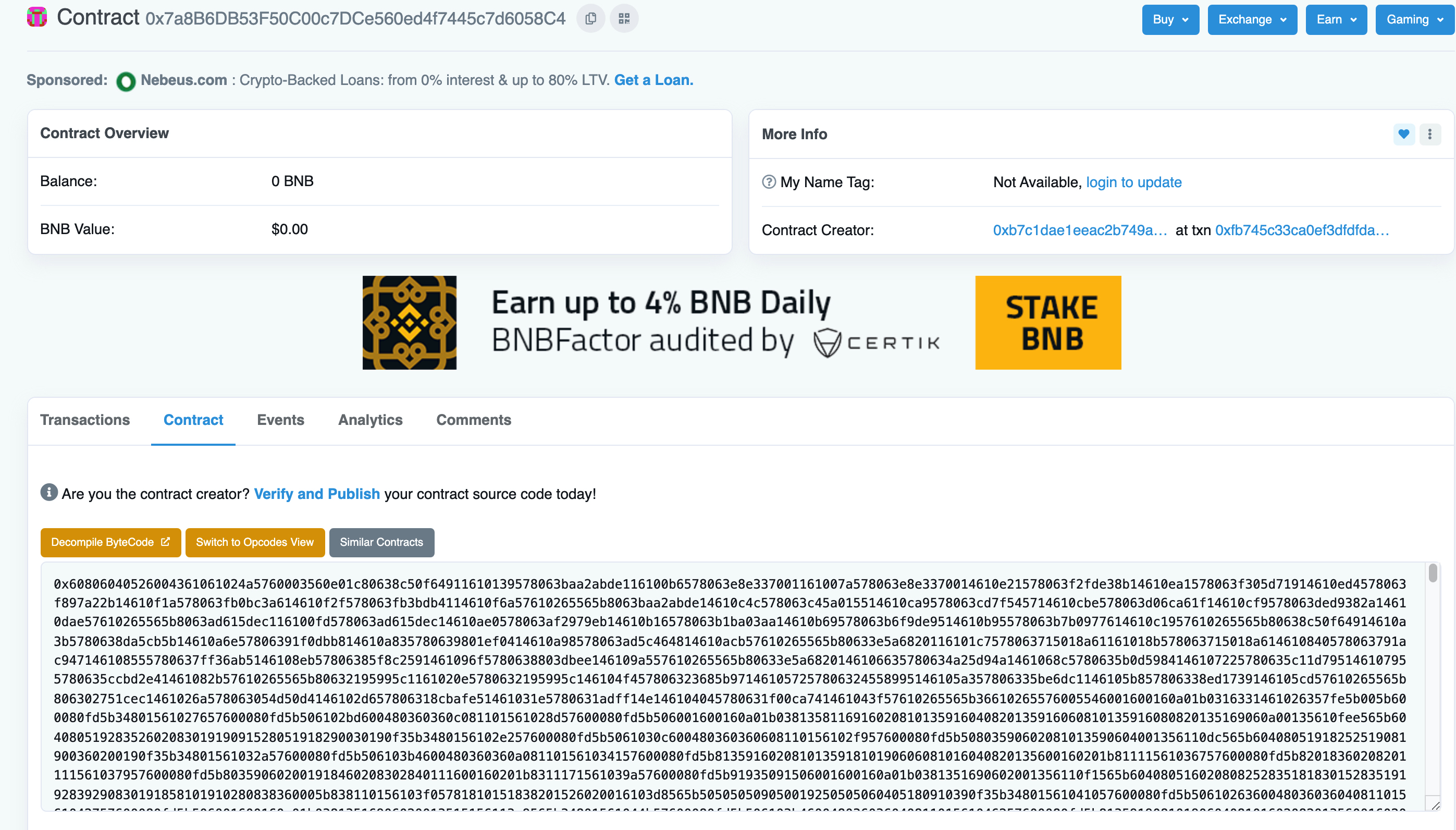
再观察一下其中一个input数据:
0x5c11d79500000000000000000000000000000000000000000000065a4da25d3016c00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000a0000000000000000000000000c6ce2918d13b7983fa6c305e726c3dc4c805b42100000000000000000000000000000000000000000000000000000000615fe5380000000000000000000000000000000000000000000000000000000000000002000000000000000000000000acb8f52dc63bb752a51186d1c55868adbffee9c1000000000000000000000000197ea04912dc81fcd19992e6210168109aa9c3fe
最后一段数据是 回购宝石代币的代币地址
暂且判断最后一段数据,是哪个代币地址,则是回购了哪个代币
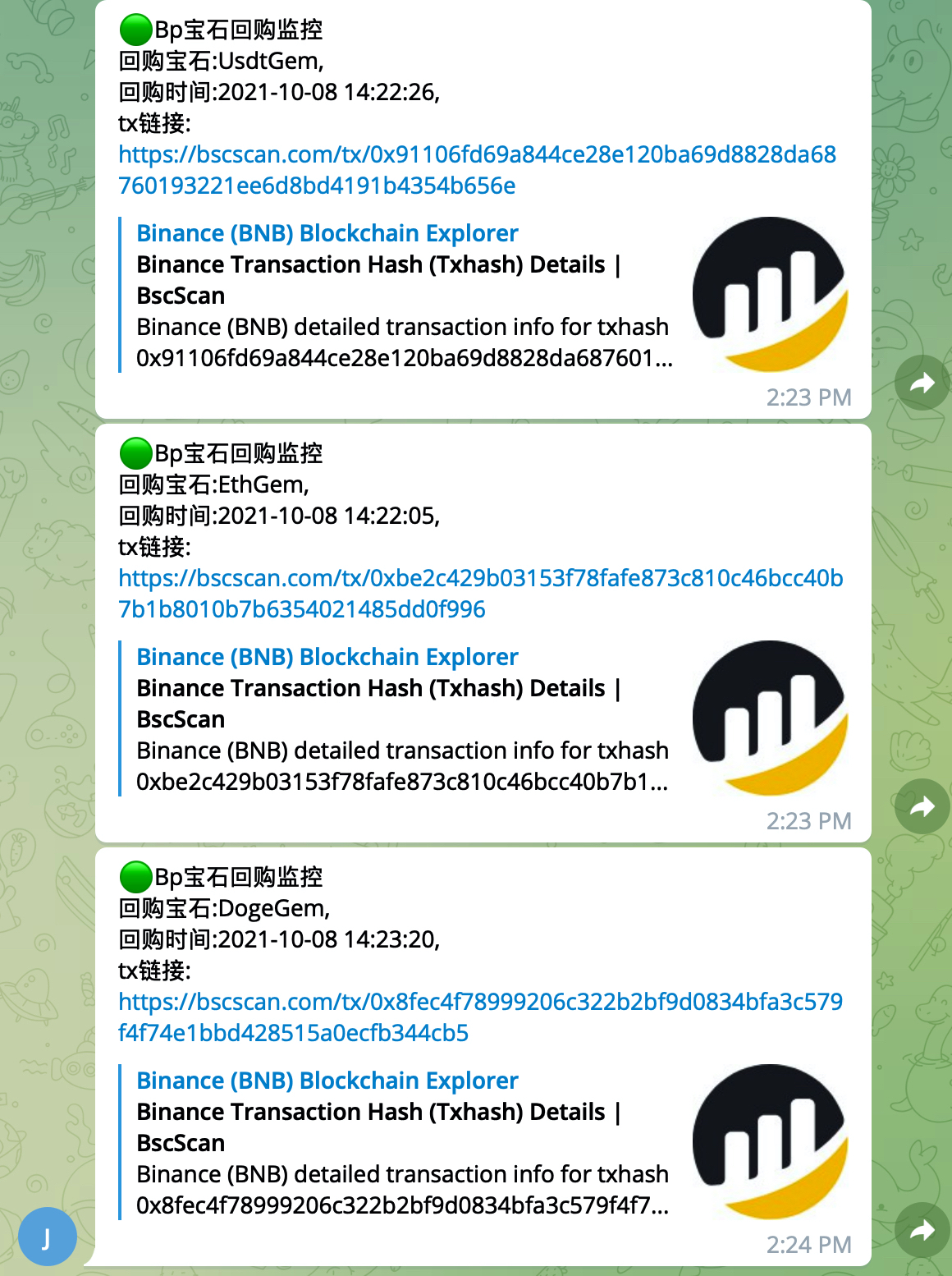
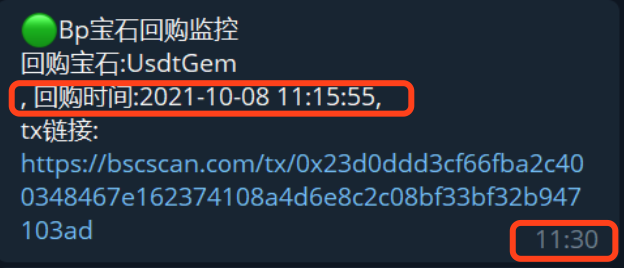
效果:
定时任务+tg提醒
Bug:
刚开始跑的时候,发现有延迟
https://api.bscscan.com/api?module=account&action=txlist&address=0xF426a8d0A94bf039A35CEE66dBf0227A7a12D11e&startblock=0&endblock=99999999&page=1&offset=10&sort=asc&apikey=YourApiKeyToken
猜测是startblock参数造成的,不要从0区块开始查,后续每次跑的时候都更新一下这个参数即可。
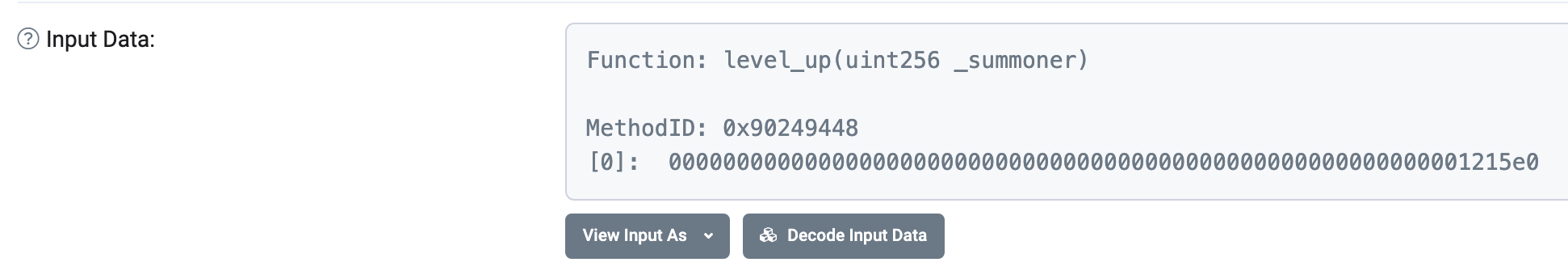
decode input data试验:
1 | # python |
在有abi的情况下,确实是可以解出input data的
1 | (<Function level_up(uint256)>, {'_summoner': 1185248}) |