1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
| {
"source": "NVD",
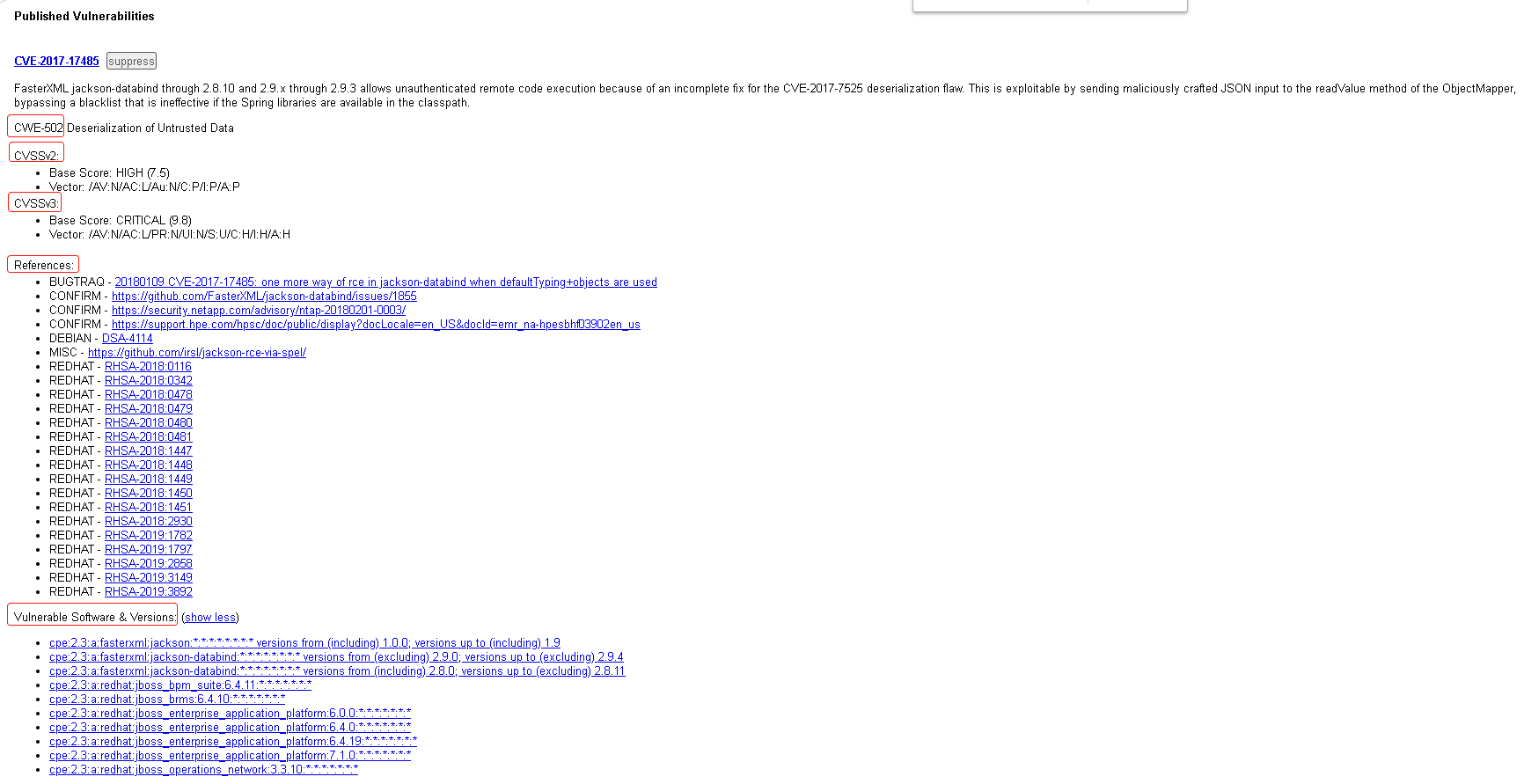
"name": "CVE-2017-17485",
"severity": "CRITICAL",
"cvssv2": {
"score": 7.5,
"accessVector": "NETWORK",
"accessComplexity": "LOW",
"authenticationr": "NONE",
"confidentialImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"availabilityImpact": "PARTIAL",
"severity": "HIGH"
},
"cvssv3": {
"baseScore": 9.8,
"attackVector": "NETWORK",
"attackComplexity": "LOW",
"privilegesRequired": "NONE",
"userInteraction": "NONE",
"scope": "UNCHANGED",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"availabilityImpact": "HIGH",
"baseSeverity": "CRITICAL"
},
"cwes": [
"CWE-502"
],
"description": "FasterXML jackson-databind through 2.8.10 and 2.9.x through 2.9.3 allows unauthenticated remote code execution because of an incomplete fix for the CVE-2017-7525 deserialization flaw. This is exploitable by sending maliciously crafted JSON input to the readValue method of the ObjectMapper, bypassing a blacklist that is ineffective if the Spring libraries are available in the classpath.",
"notes": "",
"references": [
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2019:3149",
"name": "RHSA-2019:3149"
},
{
"source": "CONFIRM",
"url": "https:\/\/support.hpe.com\/hpsc\/doc\/public\/display?docLocale=en_US&docId=emr_na-hpesbhf03902en_us",
"name": "https:\/\/support.hpe.com\/hpsc\/doc\/public\/display?docLocale=en_US&docId=emr_na-hpesbhf03902en_us"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2018:1449",
"name": "RHSA-2018:1449"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2018:0342",
"name": "RHSA-2018:0342"
},
{
"source": "MISC",
"url": "https:\/\/github.com\/irsl\/jackson-rce-via-spel\/",
"name": "https:\/\/github.com\/irsl\/jackson-rce-via-spel\/"
},
{
"source": "CONFIRM",
"url": "https:\/\/security.netapp.com\/advisory\/ntap-20180201-0003\/",
"name": "https:\/\/security.netapp.com\/advisory\/ntap-20180201-0003\/"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2019:1782",
"name": "RHSA-2019:1782"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2019:2858",
"name": "RHSA-2019:2858"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2018:0478",
"name": "RHSA-2018:0478"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2018:0481",
"name": "RHSA-2018:0481"
},
{
"source": "CONFIRM",
"url": "https:\/\/github.com\/FasterXML\/jackson-databind\/issues\/1855",
"name": "https:\/\/github.com\/FasterXML\/jackson-databind\/issues\/1855"
},
{
"source": "BUGTRAQ",
"url": "http:\/\/www.securityfocus.com\/archive\/1\/541652\/100\/0\/threaded",
"name": "20180109 CVE-2017-17485: one more way of rce in jackson-databind when defaultTyping+objects are used"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2018:0480",
"name": "RHSA-2018:0480"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2018:2930",
"name": "RHSA-2018:2930"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2018:0116",
"name": "RHSA-2018:0116"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2018:1447",
"name": "RHSA-2018:1447"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2018:1450",
"name": "RHSA-2018:1450"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2019:3892",
"name": "RHSA-2019:3892"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2019:1797",
"name": "RHSA-2019:1797"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2018:0479",
"name": "RHSA-2018:0479"
},
{
"source": "DEBIAN",
"url": "https:\/\/www.debian.org\/security\/2018\/dsa-4114",
"name": "DSA-4114"
},
{
"source": "OSSINDEX",
"url": "https:\/\/ossindex.sonatype.org\/vuln\/b85a00e3-7d9b-49cf-9b19-b73f8ee60275",
"name": "[CVE-2017-17485] Improper Control of Generation of Code (\"Code Injection\")"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2018:1448",
"name": "RHSA-2018:1448"
},
{
"source": "REDHAT",
"url": "https:\/\/access.redhat.com\/errata\/RHSA-2018:1451",
"name": "RHSA-2018:1451"
}
],
"vulnerableSoftware": [
{
"software": {
"id": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"vulnerabilityIdMatched": "true",
"versionStartExcluding": "2.9.0",
"versionEndExcluding": "2.9.4"
}
},
{
"software": {
"id": "cpe:2.3:a:redhat:jboss_bpm_suite:6.4.11:*:*:*:*:*:*:*"
}
},
{
"software": {
"id": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:6.0.0:*:*:*:*:*:*:*"
}
},
{
"software": {
"id": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:6.4.0:*:*:*:*:*:*:*"
}
},
{
"software": {
"id": "cpe:2.3:a:redhat:jboss_brms:6.4.10:*:*:*:*:*:*:*"
}
},
{
"software": {
"id": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:7.1.0:*:*:*:*:*:*:*"
}
},
{
"software": {
"id": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"versionStartIncluding": "2.8.0",
"versionEndExcluding": "2.8.11"
}
},
{
"software": {
"id": "cpe:2.3:a:fasterxml:jackson:*:*:*:*:*:*:*:*",
"versionStartIncluding": "1.0.0",
"versionEndIncluding": "1.9"
}
},
{
"software": {
"id": "cpe:2.3:a:redhat:jboss_enterprise_application_platform:6.4.19:*:*:*:*:*:*:*"
}
},
{
"software": {
"id": "cpe:2.3:a:redhat:jboss_operations_network:3.3.10:*:*:*:*:*:*:*"
}
}
|